Longview SSO Service Installation
The Longview Single Sign-On Service enables users to use SAML or OpenID/OAuth protocols for their Single Sign on solution. The Single Sign-On Service can be shared between your multiple instances of Longview and does not need to be installed on the same machine as your Longview Servers.
The following diagram shows you how the SAML authentication flow works with Longview:
SAML Authentication Flow Diagram
Installing Longview Single sign-on Service
The following steps are to be done on the server that will host the Longview single sign-on service:
- Download and install Node.js, version v20.12.2 (LTS) or later, from the npm website.
- Create a folder to setup the Longview single sign-on in, for example
C:\Longview\SSO. - Unzip the Longview SSO Service .zip into the folder created in the previous step.
- Rename
config_template.jsontoconfig.json - Open the
config.jsonand set the parameters as listed below. - Once the changes have been made, save, and close the
config.jsonfile.
Settings for all configuration types
| Parameter | Description |
|---|---|
| relayUrls |
Specify the URL to the Longview Servers' web bridge that are going to use single sign-on authentication. Example: This parameter supports multiple URLs. You can add the Longview Data server web bridge for the additional Longview data servers that will use this Longview SSO service. Only Longview Servers with URL registered in the list can authenticate against the SSO service |
| port |
This is the port the Longview SSO service will use to communicate on. The default is 4000. |
| refreshSchedule |
This is an optional parameter. If it is not set it will be ignored. This parameter schedules a job at a specified time to refresh the services configuration, ensuring that any changes take effect. The value of this parameter must be set using cron-style scheduling. For example, 1 refresh every 10 minutes would be set to:
For more information on cron-style schedule syntax, refer to https://www.npmjs.com/package/node-schedule |
 Settings for Proxy
Settings for Proxy
| Parameter | Value |
|---|---|
| URL |
This is an optional parameter that only needs to be set if the host environment of the Longview SSO service enforces all outbound HTTP/HTTPS requests to route through a proxy server. If your company requires all outbound traffic to go through a proxy, specify the proxy server address. This allows the Longview SSO service to successfully communicate with the external Identity Provider (IDP). For example: "http://proxy.company.com:3128"
|
Settings for SAML
| Parameter | Value |
|---|---|
| metadataFile |
Specify the name of the metadata xml that was created from the IDP Provider. The metadata file must exist in the Longview SSO root directory. Example: Note: The Longview SSO Service will either use metadataFile or metadataUrl, if both are set then the metadataFile will be used. |
| MetadataUrl |
Specify the URL to the IDPs metadata. It is best practice to use the metadataUrl over the metadataFile to ensure that the latest metadata is always being used. Note: The Longview SSO Service will either use metadataFile or metadataUrl, if both are set then the metadataFile will be used. |
| idKey |
idKey uses the IDP application attribute that will be mapped to the Longview username. Longview recommends using the email attribute and is the default value if not specified. If your IDP application require a different attribute to be used, set this parameter to the required attribute. |
| issuer |
Set this parameter to the Audience Restriction set on the IDP SAML Application. Example of how this could be set is:
|
| callbackUrl |
Set this parameter to the Longview SSO service callback URL. For example:
|
| wantAssertionsSigned |
These parameters are optional parameters that you can modify to match your SAML IDP Application setup if you are using this additional functionality. If not, you can just leave these as their defaults. |
| wantAuthnResponseSigned | |
| failureFlash | |
| failureMessage | |
| failureRedirect |
Settings for OpenID
| Parameter | Description |
|---|---|
| issuer |
Set this parameter to the IDP URL. Example: |
| client_id |
Set this to the OpenID application ID. Example: |
| Redirect_uri |
Set this parameter to the Longview SSO service callback URL. For example:
|
| idKey |
idKey uses the IDP application attribute that will be mapped to the Longview username. Longview recommends using the email attribute and is the default value if not specified. If your IDP application require a different attribute to be used, set this parameter to the required attribute. |
Settings for OAuth
| Parameter | Value |
|---|---|
| issuer |
Set this parameter to the IDP URL. Example: |
| idKey |
idKey uses the IDP application attribute that will be mapped to the Longview username. Longview recommends using the azp attribute and is the default value if not specified. If your IDP application require a different attribute to be used, set this parameter to the required attribute. |
| audience | This is an optional parameter and only needs to be set if your using this feature in IDP application. |
| scope |
This is an optional parameter to define the permissions of the access token. Use this feature if you have defined a scope in your app api and want to restrict the permissions of the application. Note: Longview Single Sign-on Service only supports one application scope. If you want to use multiple applications with a different scope for each Data server then you will need to install multiple Longview SSO Services. |
- Open the
install.jsand replace<sso-root>with the root directory of your Longview SSO Service, for example,C:\\Longview\\sso
Note: If you want to change the name and description the Service that will be installed, you can also modify the name and description. For example you installing a second Longview SSO Service on the same machine.
10. Open a command line with Administrator privileges.
11. Run the following commands from the Longview SSO Service root directory:
npm install
node install.js
Note: To uninstall the Longview SSO Service run the following in the command line with Administrator privileges:
node uninstall.js
Setting up Longview SSO proxy
- On the SSO web server, install Microsoft's Application Request Routing extension for IIS. You can download this extension from: http://www.iis.net/downloads/microsoft/applicationrequest-routing
- On the SSO web Server, open Internet Information Services (IIS) Manager.
- In the Connections pane, select the Web Server Root.
- In the content pane, double click Configuration Editor.
- Select
system.webServer/proxy - Set
preserveHostHeadertoTrueand click Apply to save the changes. - In the Connections pane, navigate to, and select the appropriate web server.
- In the content pane, double click URL Rewrite.
- In the Action pane, click Reverse Proxy.
- Enter
localhost:4000in the Inbound Rules edit box.Note: Localhost could be set to the Longview Web Server if it's not on the same machine as the Longview SSO Service.
4000 is the default port used for setup, if you provided a different port during setup then specify the port that was used.
- Click OK to save.
- Double click on the rule that was created to modify it.
- Update the Pattern to contain
sso/(.*) - Click Apply to save then changes, and then click Back to Rules to return to the contents window.
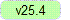 Longview SSO Service Version Verification
Longview SSO Service Version Verification
To verify the Longview Single Sign-On (SSO) service version, please follow the steps below:
1. Navigate to the folder where you set up the Longview SSO Service (for example, C:\Longview\SSO). For more information, refer to Installing Longview Single Sign-On Service.
2. Open the sso.log file.
3. In the sso.log file, locate the Longview SSO Service version number, which is logged during the service startup.
Configuring the Longview Data Servers
- Open the
lvsrvr.cfgfor the Longview Data Servers that will use single sign-on authorization. - Set the following and save the
lvsrvr.cfg.Parameter Value SSO_SERVICE_URL Set to the URL to the Longview SSO Web Service. The URL will either be setup for saml or openid.
For example:
SAML:
https://srvr1201sql01.domain.com/sso/samlOpenID:
https://srvr1201sql01.domain.com/sso/openid - Restart the Longview Data Servers for the changes to take effect.